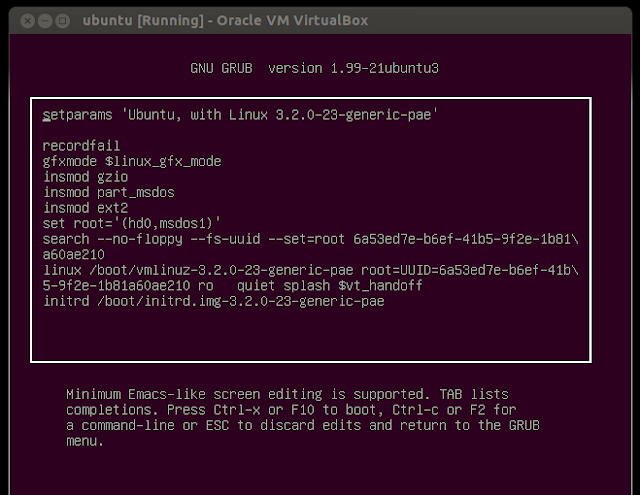
While your system booting hold the Shift Key. You will get the GRUB screen like below
Select the first Grub entry and press e to edit the the Grub entry that splash screen like below
Find and change the line
linux /boot/vmlinuz-3.2.0-23-generic-pae root=UUID=xxxxxxxx-xxxx-xxxx-xxxxxxxxxxxx ro quiet splash to linux /boot/vmlinuz-3.2.0-23-generic-pae root=UUID=xxxxxxxx-xxxx-xxxx-xxxxxxxxxxxx rw init=/bin/bash
After changed above line Press crtl+x or F10 to boot. Now you logged in without password
Now you can able to reset the root password using following command
Enjoy....
Select the first Grub entry and press e to edit the the Grub entry that splash screen like below
Find and change the line
linux /boot/vmlinuz-3.2.0-23-generic-pae root=UUID=xxxxxxxx-xxxx-xxxx-xxxxxxxxxxxx ro quiet splash to linux /boot/vmlinuz-3.2.0-23-generic-pae root=UUID=xxxxxxxx-xxxx-xxxx-xxxxxxxxxxxx rw init=/bin/bash
After changed above line Press crtl+x or F10 to boot. Now you logged in without password
Now you can able to reset the root password using following command
Enjoy....